User
Since I am no edge lord that purely uses
masscan
for network enumeration, I fired up Nmap to see what services were running on the box.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-10 08:26 AWST
Nmap scan report for delivery.htb (10.10.10.222)
Host is up (0.061s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
8065/tcp open unknown
| fingerprint-strings:
| GenericLines, Help, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Cache-Control: no-cache, max-age=31556926, public
| Content-Length: 3108
| Content-Security-Policy: frame-ancestors 'self'; script-src 'self' cdn.rudderlabs.com
| Content-Type: text/html; charset=utf-8
| Last-Modified: Sat, 09 Jan 2021 19:00:51 GMT
| X-Frame-Options: SAMEORIGIN
| X-Request-Id: i3xa8qsmtiyoum5gfzo5bp6h8c
| X-Version-Id: 5.30.0.5.30.1.57fb31b889bf81d99d8af8176d4bbaaa.false
| Date: Sun, 10 Jan 2021 00:26:57 GMT
| <!doctype html><html lang="en"><head><meta charset="utf-8"><meta name="viewport" content="width=device-width,initial-scale=1,maximum-scale=1,user-scalable=0"><meta name="robots" content="noindex, nofollow"><meta name="referrer" content="no-referrer"><title>Mattermost</title><meta name="mobile-web-app-capable" content="yes"><meta name="application-name" content="Mattermost"><meta name="format-detection" content="telephone=no"><link re
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Date: Sun, 10 Jan 2021 00:26:57 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8065-TCP:V=7.91%I=7%D=1/10%Time=5FFA49B4%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x
SF:20Request")%r(GetRequest,DF3,"HTTP/1\.0\x20200\x20OK\r\nAccept-Ranges:\
SF:x20bytes\r\nCache-Control:\x20no-cache,\x20max-age=31556926,\x20public\
SF:r\nContent-Length:\x203108\r\nContent-Security-Policy:\x20frame-ancesto
SF:rs\x20'self';\x20script-src\x20'self'\x20cdn\.rudderlabs\.com\r\nConten
SF:t-Type:\x20text/html;\x20charset=utf-8\r\nLast-Modified:\x20Sat,\x2009\
SF:x20Jan\x202021\x2019:00:51\x20GMT\r\nX-Frame-Options:\x20SAMEORIGIN\r\n
SF:X-Request-Id:\x20i3xa8qsmtiyoum5gfzo5bp6h8c\r\nX-Version-Id:\x205\.30\.
SF:0\.5\.30\.1\.57fb31b889bf81d99d8af8176d4bbaaa\.false\r\nDate:\x20Sun,\x
SF:2010\x20Jan\x202021\x2000:26:57\x20GMT\r\n\r\n<!doctype\x20html><html\x
SF:20lang=\"en\"><head><meta\x20charset=\"utf-8\"><meta\x20name=\"viewport
SF:\"\x20content=\"width=device-width,initial-scale=1,maximum-scale=1,user
SF:-scalable=0\"><meta\x20name=\"robots\"\x20content=\"noindex,\x20nofollo
SF:w\"><meta\x20name=\"referrer\"\x20content=\"no-referrer\"><title>Matter
SF:most</title><meta\x20name=\"mobile-web-app-capable\"\x20content=\"yes\"
SF:><meta\x20name=\"application-name\"\x20content=\"Mattermost\"><meta\x20
SF:name=\"format-detection\"\x20content=\"telephone=no\"><link\x20re")%r(H
SF:TTPOptions,5B,"HTTP/1\.0\x20405\x20Method\x20Not\x20Allowed\r\nDate:\x2
SF:0Sun,\x2010\x20Jan\x202021\x2000:26:57\x20GMT\r\nContent-Length:\x200\r
SF:\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConten
SF:t-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n
SF:400\x20Bad\x20Request")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close
SF:\r\n\r\n400\x20Bad\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x2
SF:0Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nCon
SF:nection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TerminalServerCookie
SF:,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;
SF:\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request"
SF:);
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 92.86 seconds
The first thing that I looked at was the weird web service running on port
8065
.
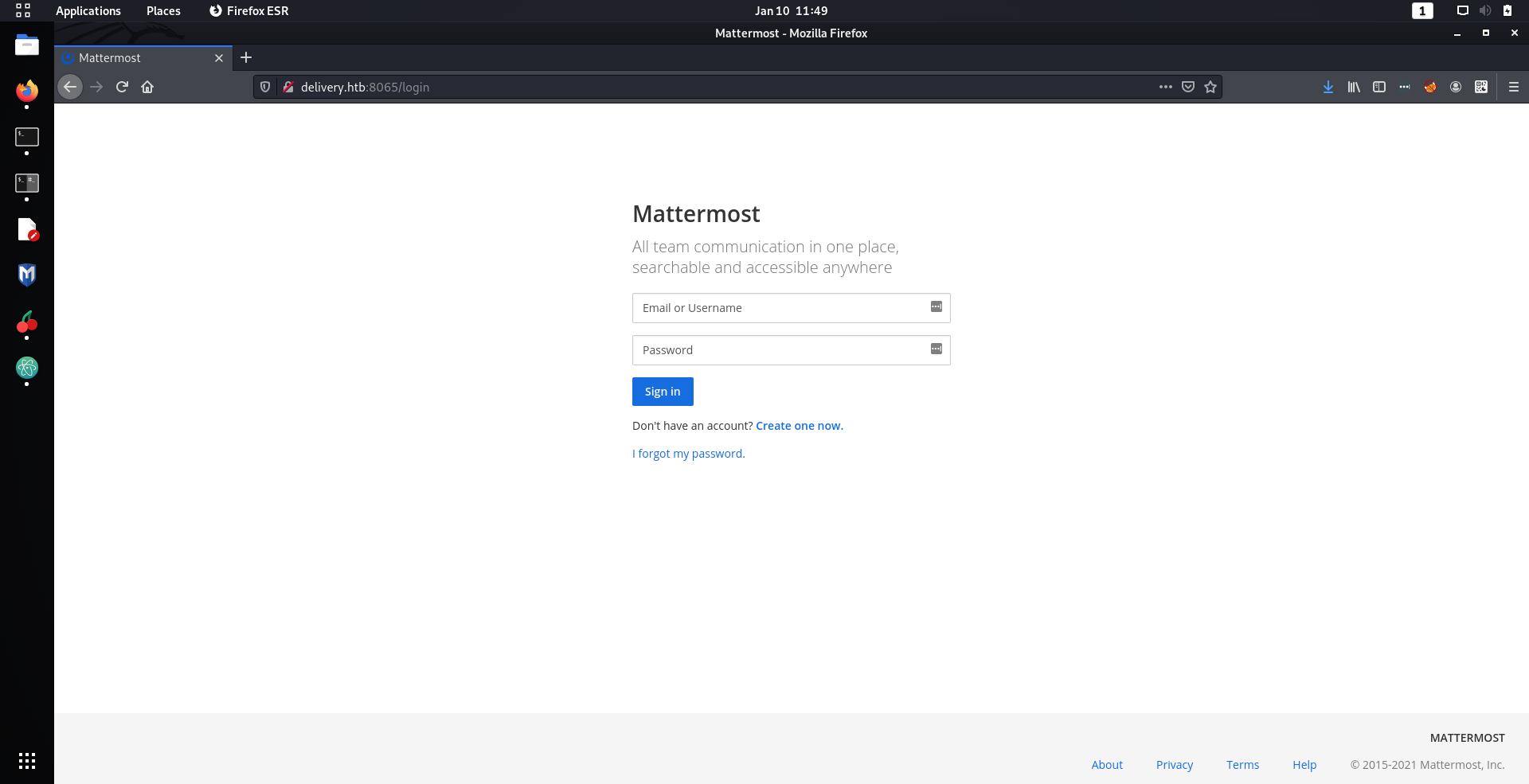
Turned out it was MatterMost, which is an Open Source equivalent to Slack. Initially I tried to create an account to get in, but unfortunately it required email confirmation. Welp that would not be the way in, so I decided to look at the website on port
80
instead. I immediately noticed the extremely interesting contact us page on the site.
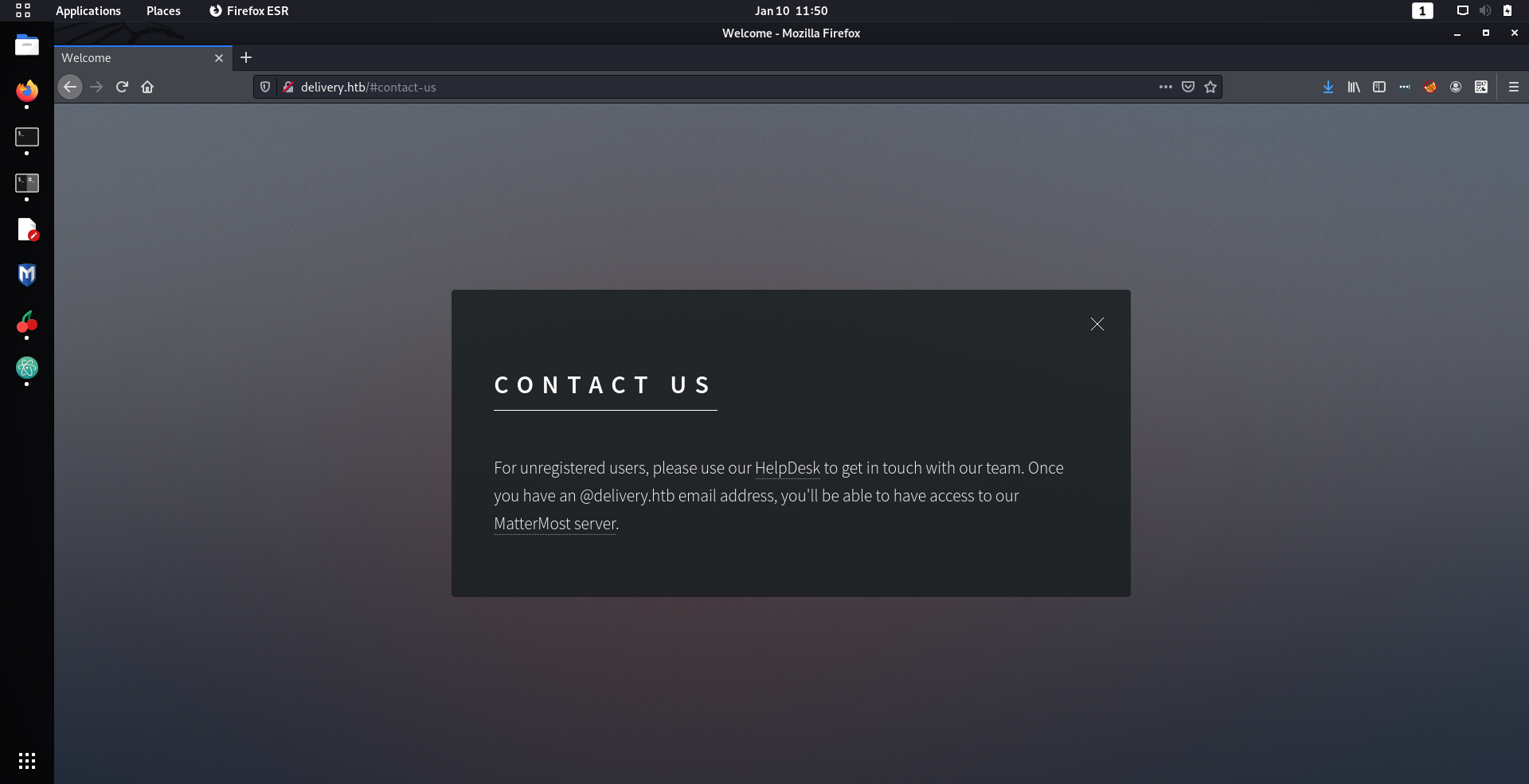
That small paragraph was packed with so much
juicy
information. Firstly it revealed that there was a web server running on
helpdesk.delivery.htb
and secondly an email with the domain
delivery.htb
was required to get access to the MatterMost site. So I decided take a closer look at their help desk service.
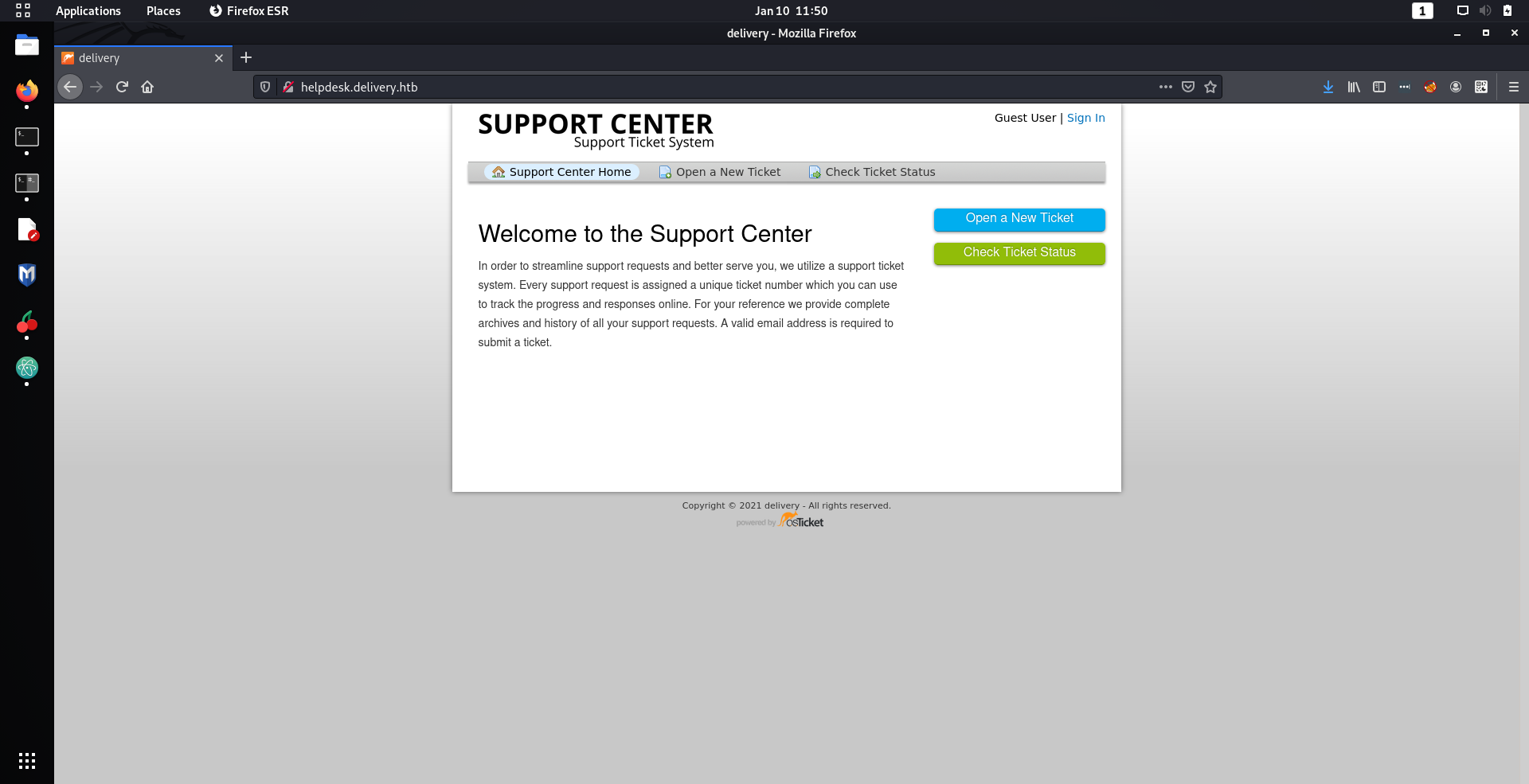
Looks like it was a ticket support center using osTicket. I did some quick research to find if there were any CVEs for osTicket, mainly because about 99% of the easy boxes on HackTheBox required using some CVE. However, this was
surprisingly
fruitless.
The next thing I tried was to see what I could do on the support center. I could not create an account on osTicket, because it required a confirmation email just like the MatterMost site
(damn)
. But I can create support tickets, which I thought was interesting.
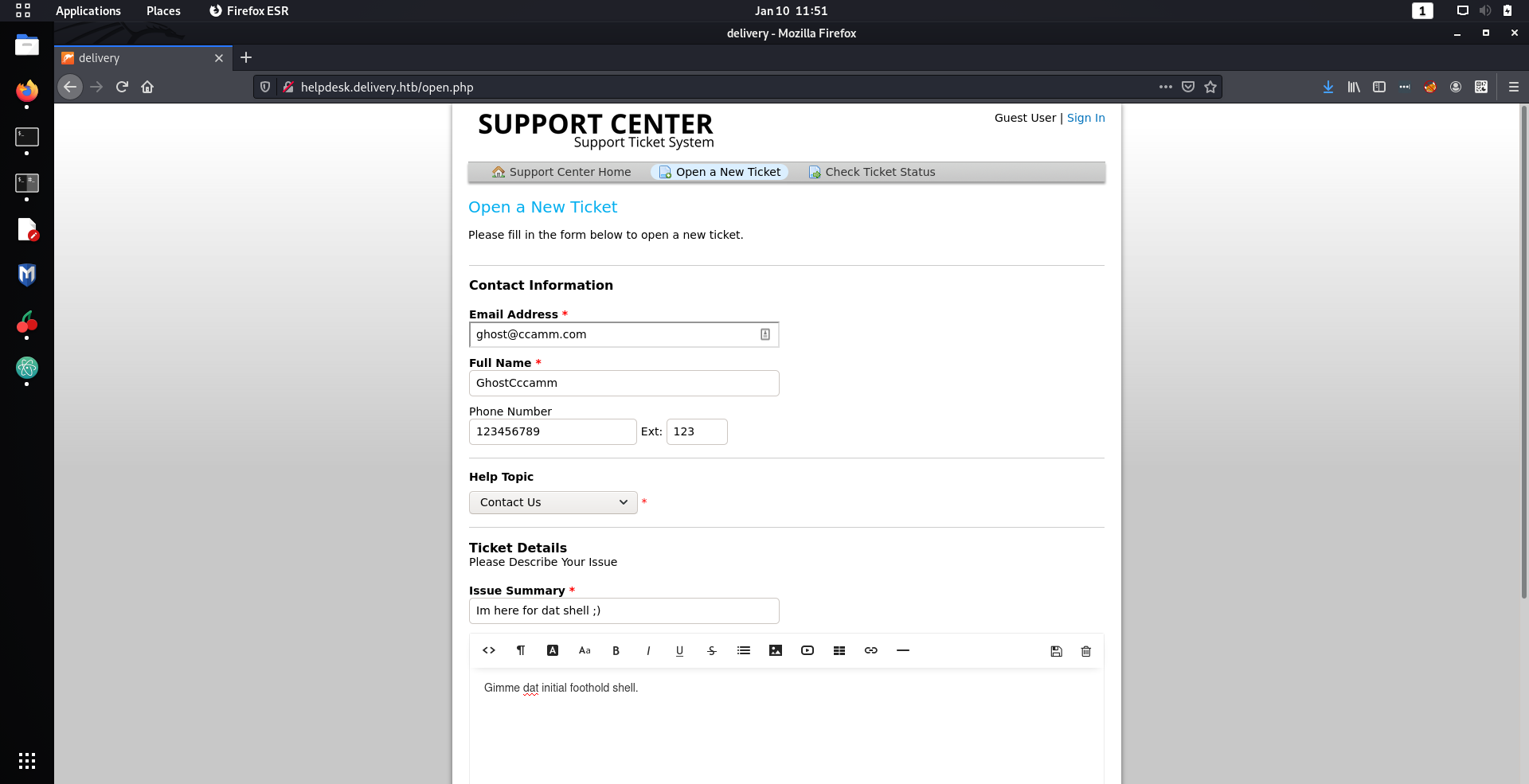
Once my ticket was created I got the following confirmation message.
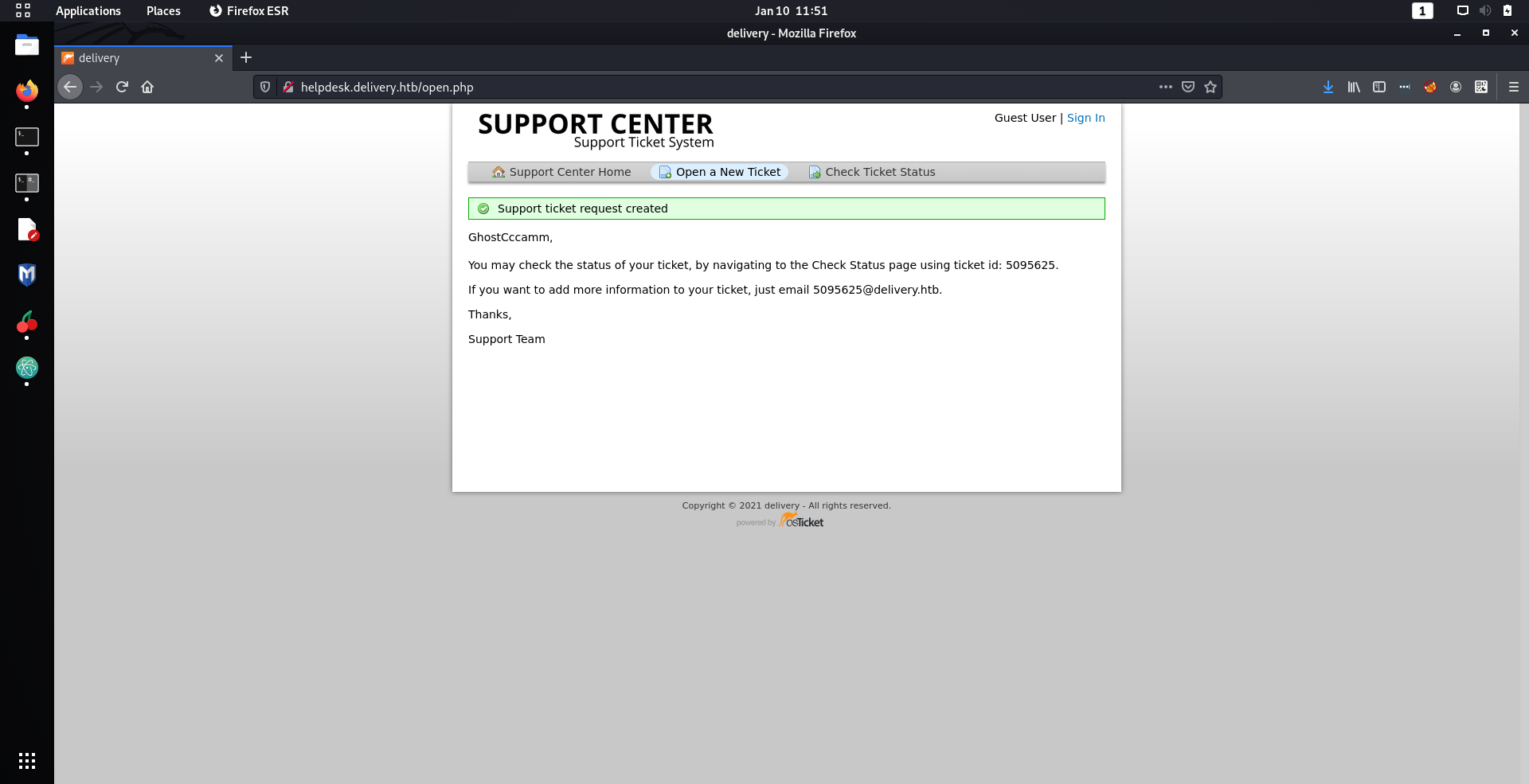
Unfortunately for me, I did not immediately notice the
JUICIEST
nugget of information that was just in front of me and wasted half an hour. The nugget was that when I submitted a ticket,
I am given an email address with the
delivery.htb
domain that I could use for account confirmation on the MatterMost site!
Emails sent to the ticket email would then be shown on the ticket that I had submitted, and would therefore reveal the registration link I need to create an account.
So I went back to the MatterMost website and created an account with the email that was generated when I created my ticket. Viewing the ticket on the support center website I could now see the contents of the registration email and successfully created my account on the MatterMost site.
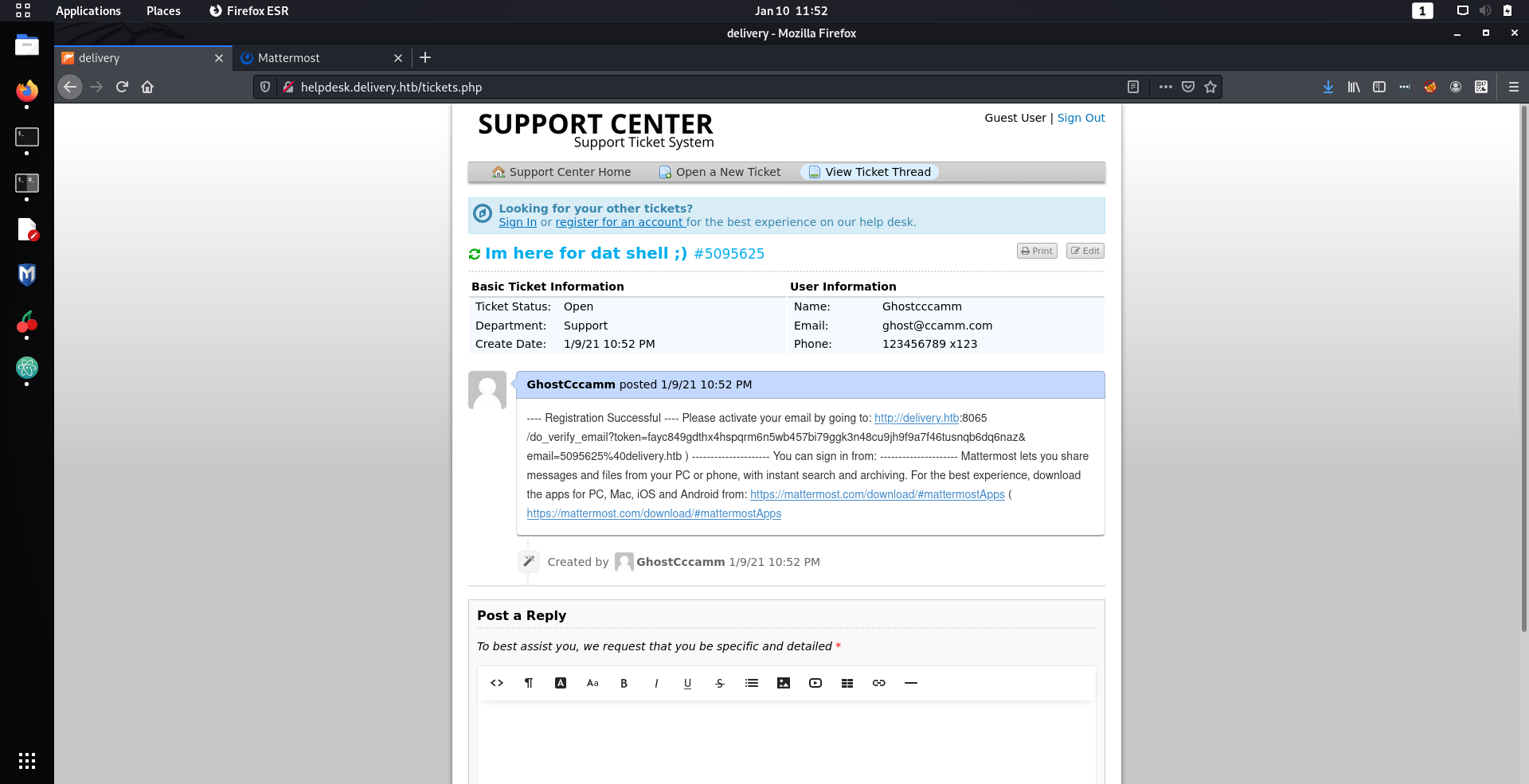
Nnoooooooooooiiiiiice
Once I created an account on the MatterMost site I was immediately shown some messages that should definitely not be sent on channels.
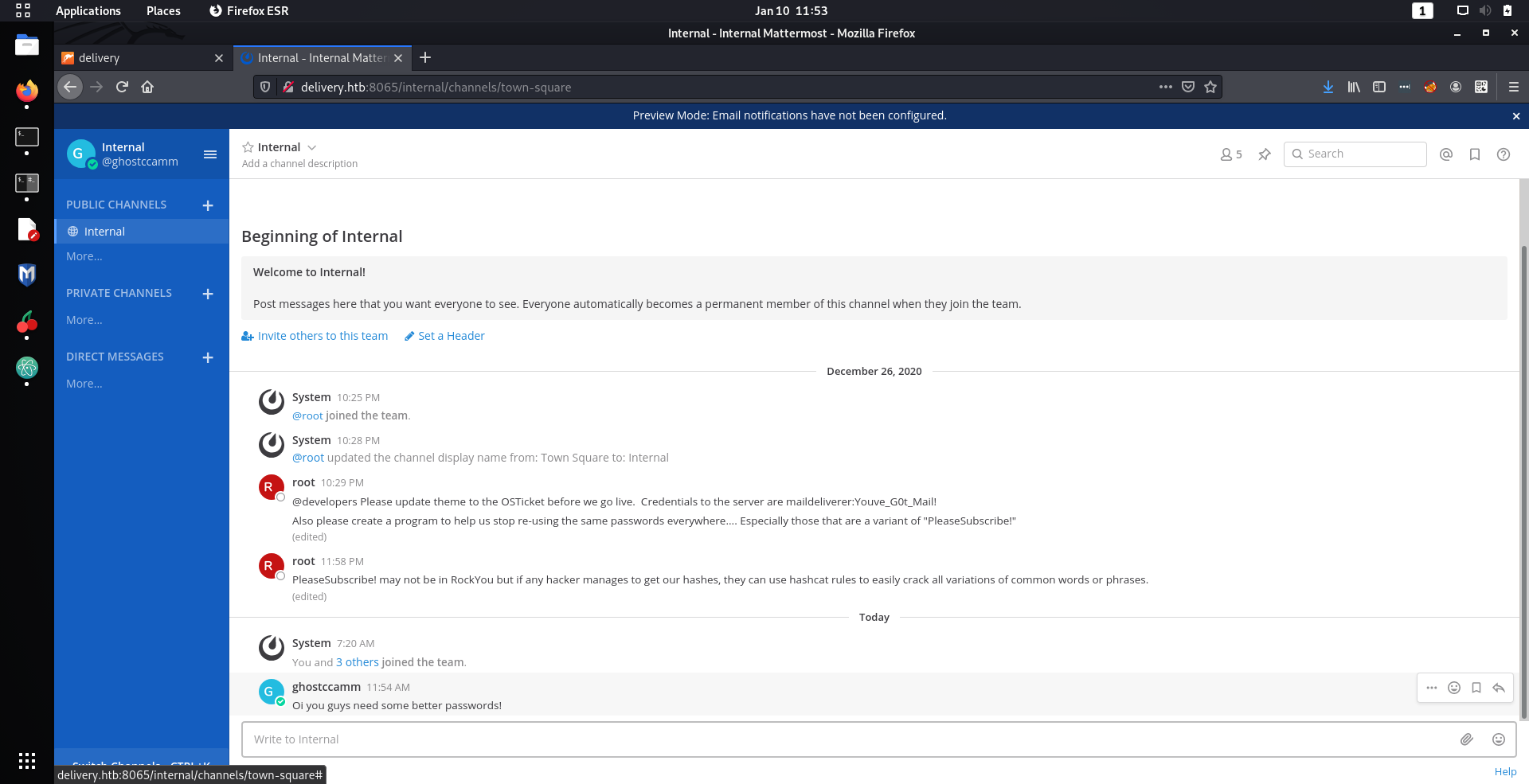
Wow such bad opsec...
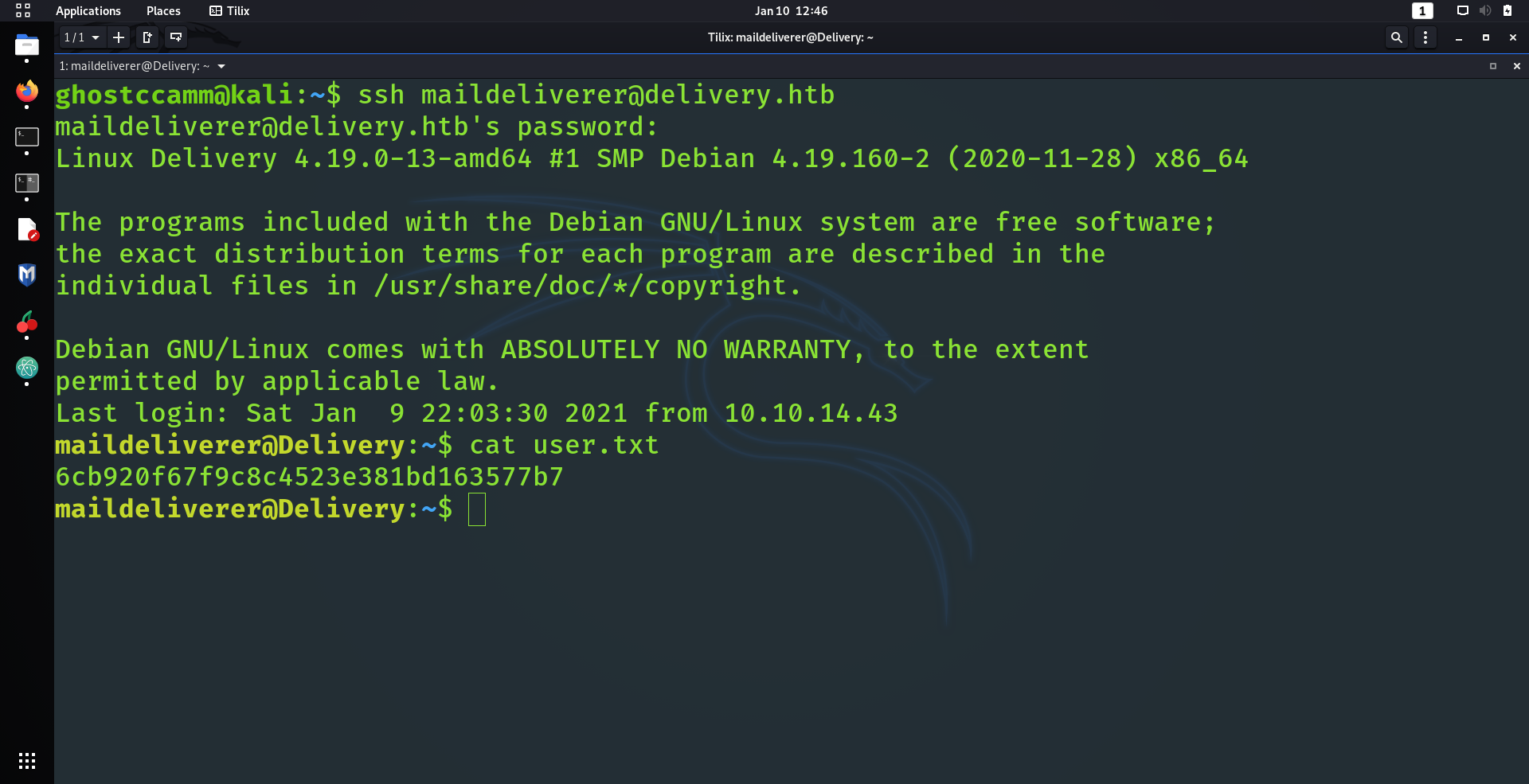
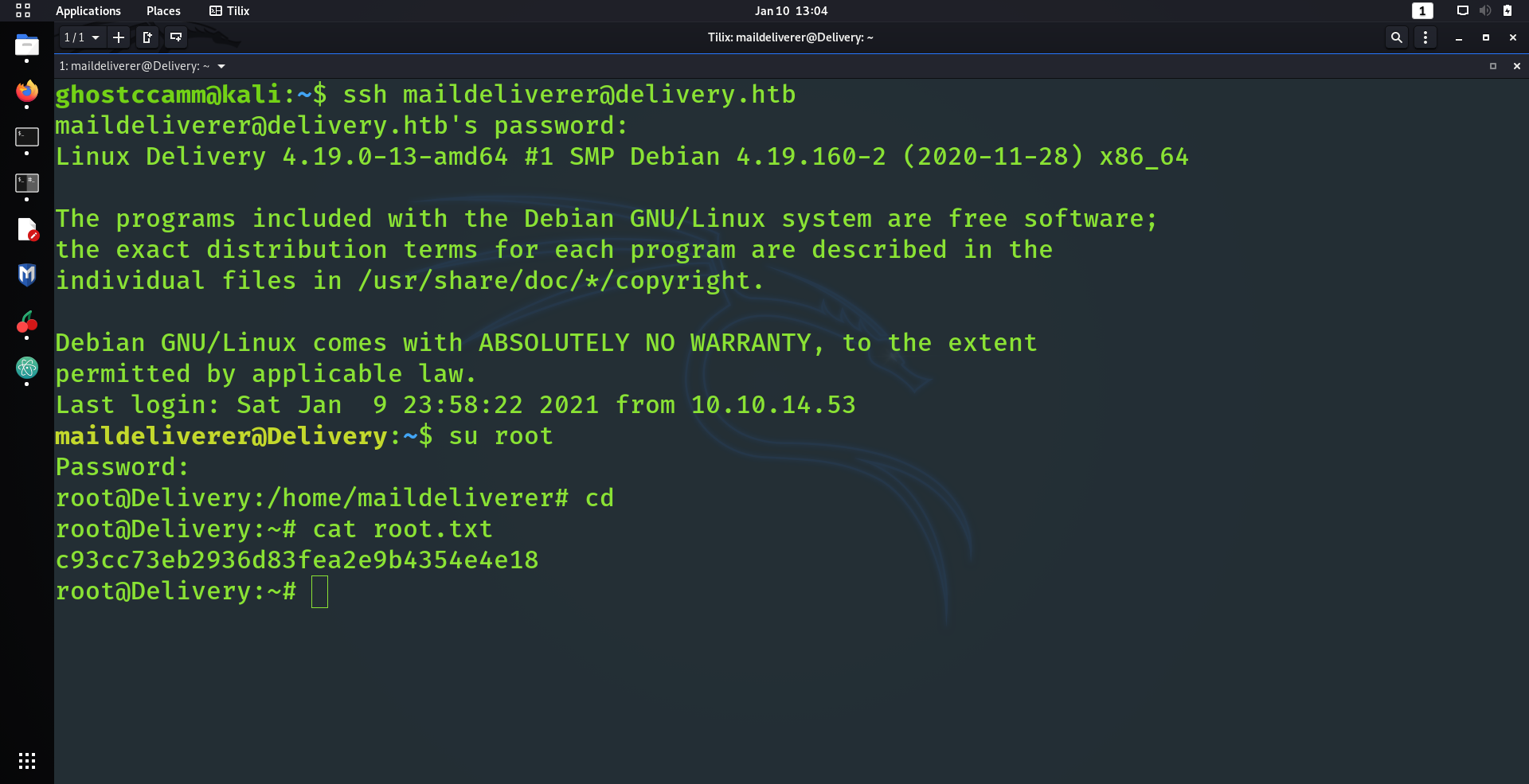
Anyway, I tried to SSH into the machine using the credentials that were sent by
root
(
maildeliverer:Youve_G0t_Mail!
) and
BAM
I got in!